and how to handle them
In our previous post “Resilience and the Crucial Role of ITGCs in Risk Mitigation“, we mentioned ITGC challenges that most organizations face.

Let’s explore each of these challenges and how to address them
1 Rapid Technological Changes
Maintaining alignment of IT General Controls (ITGCs) in an ever-evolving IT landscape requires a strategic and proactive approach. Firstly, organizations should establish a continuous monitoring system to promptly identify and adapt to changes in technology, ensuring that control measures remain effective. Secondly, regularly update ITGC policies and procedures to reflect the evolving IT environment, and provide ongoing training for personnel to stay abreast of emerging risks and best practices. This dynamic and adaptive approach ensures that ITGCs remain robust and aligned with the constantly changing technological landscape.
2 Complexities in Change Management
Implementing an effective change management process is essential for organizations to navigate transitions successfully. There are many methodologies to choose from such as –
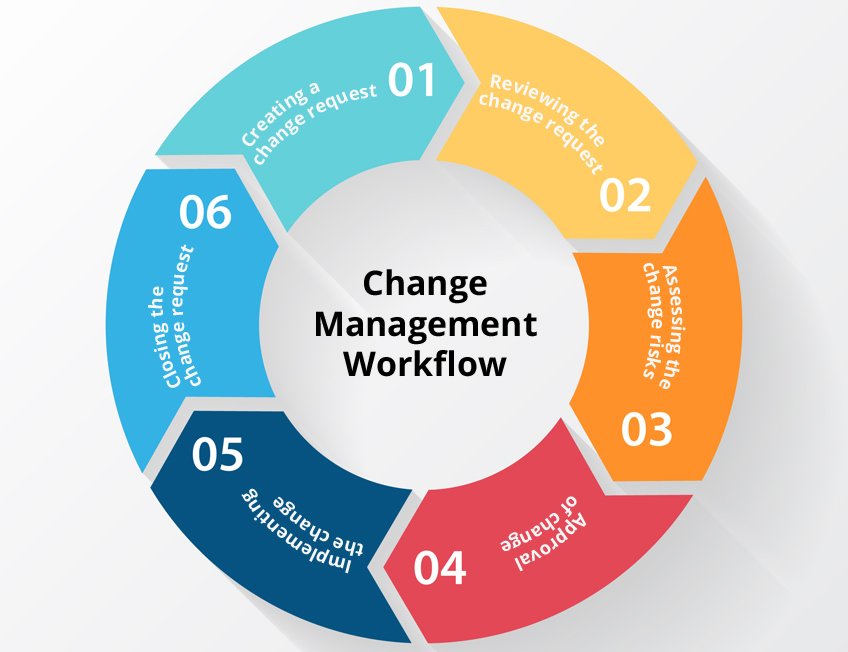
ITIL – The ITIL (Information Technology Infrastructure Library) Change Management model is a part of the broader ITIL framework, which provides a set of best practices for IT service management (ITSM). The Change Management process within ITIL focuses on controlling the lifecycle of all changes within an IT environment to minimize disruptions, improve service quality, and ensure alignment with business goals.

AGILE – Agile Change Management is an approach to organizational change that draws inspiration from Agile methodologies commonly used in software development. It applies the principles of flexibility, collaboration, and iterative development to manage change initiatives in a more adaptive and responsive manner. The traditional change management processes often face challenges in dynamic and rapidly changing environments, and Agile Change Management aims to address these issues.
3 Continuous Monitoring
Continuous monitoring ensures effective operation of IT General Controls (ITGCs) by collecting real-time data, utilizing automated tools for analysis, logging security events, monitoring user activities, conducting vulnerability scans, facilitating incident detection and response, ensuring compliance, utilizing dashboards for reporting, setting up automated alerts, and promoting continuous improvement. This systematic approach promptly identifies and addresses potential security issues, contributing to a robust IT environment.
Real-Time Data Collection
Continuous monitoring involves the continuous collection of data related to ITGCs. This data may include information on user access, system configurations, security events, and other relevant parameters.
Automated Tools and Technologies
Automated monitoring tools are often employed to collect and analyze data continuously. These tools can provide real-time insights into the state of ITGCs, allowing organizations to respond promptly to any deviations from established controls.
Event Logging and Auditing
Continuous monitoring includes the logging and auditing of security events. Event logs are analyzed for anomalies or suspicious activities that might indicate a potential security threat or a violation of ITGCs.
User Activity Monitoring
Continuous monitoring involves tracking user activities and access to critical systems and data. Unusual patterns of user behavior or unauthorized access attempts can be quickly identified and addressed
Vulnerability Scanning
Regular and continuous vulnerability scanning helps identify weaknesses in the IT infrastructure. It allows organizations to address vulnerabilities promptly, reducing the risk of security breaches.
Incident Detection and Response
Continuous monitoring aids in the early detection of security incidents. When abnormal activities are identified, organizations can respond swiftly to mitigate the impact and investigate the root causes.
Compliance Monitoring
Continuous monitoring ensures ongoing compliance with relevant regulatory requirements and internal policies. This includes monitoring adherence to security standards, access controls, and other ITGCs.
Dashboard and Reporting
Visualization tools, dashboards, and reporting mechanisms are often used to present real-time or periodic summaries of the status of ITGCs. This allows stakeholders to quickly understand the state of controls and take necessary actions.
Automated Alerts and Notifications
Automated alerts and notifications are set up to promptly inform relevant personnel about any issues or deviations from expected norms. This enables a rapid response to potential risks or control failures.
Continuous Improvement
Continuous monitoring is not only about identifying issues but also about learning and improving. Organizations use insights gained from continuous monitoring to enhance their ITGCs, update policies, and strengthen overall security posture.
4 & 5 Balancing Access and (Cyber)Security
Achieving a balance between access and security in IT involves implementing strategies such as –
Access Governance
Role and Policy-Based Access Control
Least Privilege Principles
Segregation of Duties and Sensitive Access Controls
Strong Authentication
Automated Access Management
Security
Security Policies & Assessments
Encryption
End-Point Security Solutions
Threat Detection & Incident Response
Awareness Training
With a commitment to continuous improvement, this ensures that individuals have the necessary access while mitigating the risk of unauthorized access and enhancing overall security posture.
Reach out to learn more on how we can help your organization overcome these challenges. We are here to support you every step of the way.












